- Asa Clientless Vpn Rdp
- Cisco Asa Ssl Vpn Configuration
- Cisco Asa Vpn
- Asa Vpn Clientless
- Cisco Asa Vpn Client Download
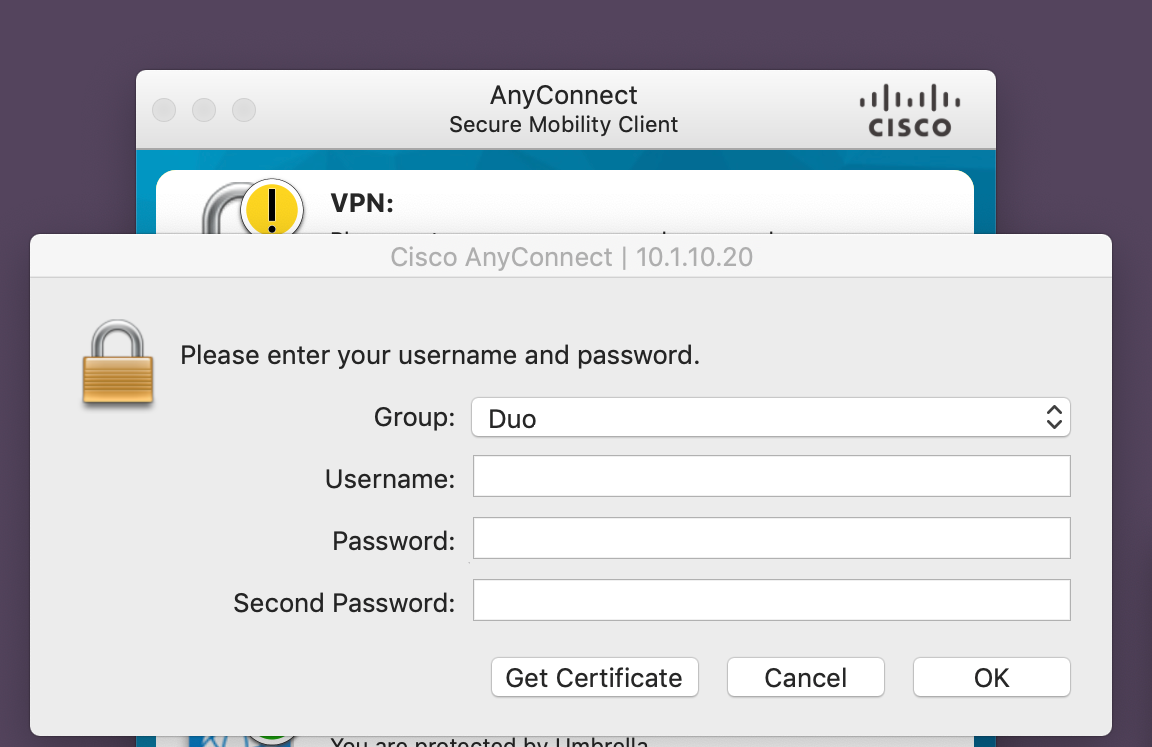
Oct 22, 2009 The Cisco IPSec VPN client does not support 64-bit operating systems. Your only option is the AnyConnect SSL client. Support for this client will require additional configuration on your headend IOS router or ASA. SRG-ASA# Configuring MAC VPN Client. Many users are now using MAC clients. Below you will find step by step instructions on configuring a MAC Client for VPN Remote Access. Open “System Preferences” and go to “Network”. Choose the add setting highlighted below, then select VPN. Configure the following VPN interface with the. When configuring the Cisco ASA 5505 as an Easy VPN hardware client, you can specify a tunnel group or trustpoint configured on the Easy VPN server. With the clientless SSL solution in the Cisco ASA firewall you will have a good complent to the client based VPN solutions such as the IPSec client.
Introduction
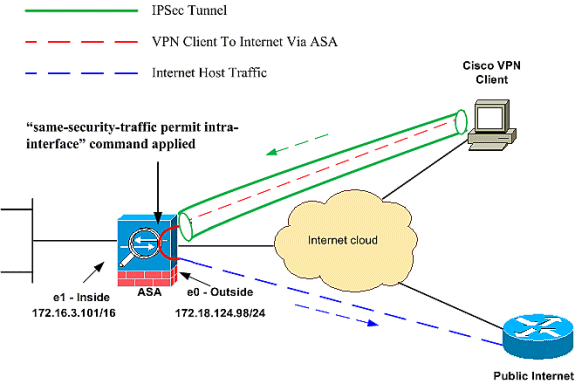
This document describes how to allow the Cisco VPN Client or the Cisco AnyConnect Secure Mobility Client to only access their local LAN while tunneled into a Cisco Adaptive Security Appliance (ASA) 5500 Series or the ASA 5500-X Series. This configuration allows Cisco VPN Clients or the Cisco AnyConnect Secure Mobility Client secure access to corporate resources via IPsec, Secure Sockets Layer (SSL), or Internet Key Exchange Version 2 (IKEv2) and still gives the client the ability to carry out activities such as printing where the client is located. If it is permitted, traffic destined for the Internet is still tunneled to the ASA.
The access-list for the 'interesting traffic' has only to match the outgoing traffic from ASA to the clients, not the traffic from the clients to the ASA. You may also use a standard access-list from the VPN traffic (which should match all hosts reachable from the clientsa through the tunnel).
Note: This is not a configuration for split tunneling, where the client has unencrypted access to the Internet while connected to the ASA or PIX. Refer to PIX/ASA 7.x: Allow Split Tunneling for VPN Clients on the ASA Configuration Example for information on how to configure split tunneling on the ASA.
Prerequisites
Requirements

This document assumes that a functional remote access VPN configuration already exists on the ASA.
Refer to PIX/ASA 7.x as a Remote VPN Server using ASDM Configuration Example for the Cisco VPN Client if one is not already configured.
Refer to ASA 8.x VPN Access with the AnyConnect SSL VPN Client Configuration Example for the Cisco AnyConnect Secure Mobility Client if one is not already configured.
Components Used
The information in this document is based on these software and hardware versions:
- Cisco ASA 5500 Series Version 9(2)1
- Cisco Adaptive Security Device Manager (ASDM) Version 7.1(6)
- Cisco VPN Client Version 5.0.07.0440
- Cisco AnyConnect Secure Mobility Client Version 3.1.05152
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Network Diagram
The client is located on a typical Small Office / Home Office (SOHO) network and connects across the Internet to the main office.
Background Information
Unlike a classic split tunneling scenario in which all Internet traffic is sent unencrypted, when you enable local LAN access for VPN clients, it permits those clients to communicate unencrypted with only devices on the network on which they are located. For example, a client that is allowed local LAN access while connected to the ASA from home is able to print to its own printer but not to access the Internet without first sending the traffic over the tunnel.
An access list is used in order to allow local LAN access in much the same way that split tunneling is configured on the ASA. However, instead of defining which networks should be encrypted, the access list in this case defines which networks should not be encrypted. Also, unlike the split tunneling scenario, the actual networks in the list do not need to be known. Instead, the ASA supplies a default network of 0.0.0.0/255.255.255.255, which is understood to mean the local LAN of the client.
Note: When the client is connected and configured for local LAN access, you cannot print or browse by name on the local LAN. However, you can browse or print by IP address. See the Troubleshoot section of this document for more information as well as workarounds for this situation.
Configure Local LAN Access for VPN Clients or the AnyConnect Secure Mobility Client
Complete these tasks in order to allow Cisco VPN Clients or Cisco AnyConnect Secure Mobility Clients access to their local LAN while connected to the ASA:
- Configure the ASA via the ASDM or Configure the ASA via the CLI
Configure the ASA via the ASDM
Complete these steps in the ASDM in order to allow VPN Clients to have local LAN access while connected to the ASA:
- Choose Configuration > Remote Access VPN > Network (Client) Access > Group Policy and select the Group Policy in which you wish to enable local LAN access. Then click Edit.
- Go to Advanced > Split Tunneling.
- Uncheck the Inherit box for Policy and choose Exclude Network List Below.
- Uncheck the Inherit box for Network List and then click Manage in order to launch the Access Control List (ACL) Manager.
- Within the ACL Manager, choose Add > Add ACL... in order to create a new access list.
- Provide a name for the ACL and click OK.
- Once the ACL is created, choose Add > Add ACE... in order to add an Access Control Entry (ACE).
- Define the ACE that corresponds to the local LAN of the client.
- Choose Permit.
- Choose an IP Address of 0.0.0.0
- Choose a Netmask of /32.
- (Optional) Provide a description.
- Click OK.
- Click OK in order to exit the ACL Manager.
- Be sure that the ACL you just created is selected for the Split Tunnel Network List.
- Click OK in order to return to the Group Policy configuration.
- Click Apply and then Send (if required) in order to send the commands to the ASA.
Configure the ASA via the CLI
Asa Clientless Vpn Rdp
Rather than use the ASDM, you can complete these steps in the ASA CLI in order to allow VPN Clients to have local LAN access while connected to the ASA:
- Enter configuration mode.
- Create the access list in order to allow local LAN access.
Caution: Due to changes in the ACL syntax between ASA software versions 8.x to 9.x, this ACL is no longer permited and admins will see this error message when they try to configure it:
rtpvpnoutbound6(config)# access-list test standard permit host 0.0.0.0
ERROR: invalid IP address
The only thing that is allowed is:
rtpvpnoutbound6(config)# access-list test standard permit any4
This is a known issue and has been addressed by Cisco bug ID CSCut3131. Upgrade to a version with the fix for this bug in order to be able to configure local LAN access. - Enter the Group Policy configuration mode for the policy that you wish to modify.
- Specify the split tunnel policy. In this case, the policy is excludespecified.
- Specify the split tunnel access list. In this case, the list is Local_LAN_Access.
- Issue this command:
- Associate the group policy with the tunnel group
- Exit the two configuration modes.
- Save the configuration to non-volatile RAM (NVRAM) and press Enter when prompted to specify the source filename.
Configure the Cisco AnyConnect Secure Mobility Client
In order to configure the Cisco AnyConnect Secure Mobility Client, refer to the Establish the SSL VPN Connection with SVC section of ASA 8.x : Allow Split Tunneling for AnyConnect VPN Client on the ASA Configuration Example.
Split-exclude tunneling requires that you enable AllowLocalLanAccess in the AnyConnect Client. All split-exclude tunneling is regarded as local LAN access. In order to use the exclude feature of split-tunneling, you must enable the AllowLocalLanAccess preference in the AnyConnect VPN Client preferences. By default, local LAN access is disabled.
In order to allow local LAN access, and therefore split-exclude tunneling, a network administrator can enable it in the profile or users can enable it in their preferences settings (see the image in the next section). In order to allow local LAN access, a user selects the Allow Local LAN access check box if split-tunneling is enabled on the secure gateway and is configured with the split-tunnel-policy exclude specified policy. In addition, you can configure the VPN Client Profile if local LAN access is allowed with <LocalLanAccess UserControllable='true'>true</LocalLanAccess>.
User Preferences
Here are the selections you should make in the Preferences tab on the Cisco AnyConnect Secure Mobility Client in order to allow local LAN access.
XML Profile Example
Here is an example of how to configure the VPN Client Profile with XML.
Verify
Complete the steps in these sections in order to verify your configuration.
Connect your Cisco AnyConnect Secure Mobility Client to the ASA in order to verify your configuration.
- Choose your connection entry from the server list and click Connect.
- Choose Advanced Window for All Components > Statistics... in order to display the Tunnel Mode.
- Click the Route Details tab in order to see the routes to which the Cisco AnyConnect Secure Mobility Client still has local access.
In this example, the client is allowed local LAN access to 10.150.52.0/22 and 169.254.0.0/16 while all other traffic is encrypted and sent across the tunnel.
Cisco AnyConnect Secure Mobility Client
When you examine the AnyConnect logs from the Diagnostics and Reporting Tool (DART) bundle, you can determine whether or not the parameter that allows local LAN access is set.
Test Local LAN Access with Ping
An additional way to test that the VPN Client still has local LAN access while tunneled to the VPN headend is to use the ping command at the Microsoft Windows command line. Here is an example where the local LAN of the client is 192.168.0.0/24 and another host is present on the network with an IP address of 192.168.0.3.
Troubleshoot
This section provides information you can use in order to troubleshoot your configuration.
Unable to Print or Browse by Name
When the VPN Client is connected and configured for local LAN access, you cannot print or browse by name on the local LAN. There are two options available in order to work around this situation:
- Browse or print by IP address.
- In order to browse, instead of the syntax sharename, use the syntax x.x.x.x where x.x.x.x is the IP address of the host computer.
- In order to print, change the properties for the network printer in order to use an IP address instead of a name. For example, instead of the syntax sharenameprintername, use x.x.x.xprintername, where x.x.x.x is an IP address.
- In order to browse, instead of the syntax sharename, use the syntax x.x.x.x where x.x.x.x is the IP address of the host computer.
- Create or modify the VPN Client LMHOSTS file. An LMHOSTS file on a Microsoft Windows PC allows you to create static mappings between hostnames and IP addresses. For example, an LMHOSTS file might look like this:
In Microsoft Windows XP Professional Edition, the LMHOSTS file is located in %SystemRoot%System32DriversEtc. Refer to your Microsoft documentation or Microsoft knowledge base Article 314108 for more information.
Related Information
- 3Gateway Configuration
- 4Client Configuration
- 4.3Authentication Tab
Introduction
This guide provides information that can be used to configure a Cisco PIX/ASA device running firmware version 7.x to support IPsec VPN client connectivity. If you have a PIX device running firmware version 6.x, please consult the HowtoCiscoPix. The Shrew Soft VPN Client has been tested with Cisco products to ensure interoperability.
Overview
The configuration example described below will allow an IPsec VPN client to communicate with a single remote private network. The client uses the pull configuration method to acquire the following parameters automatically from the gateway.
- IP Address
- IP Netmask
- DNS Servers
- DNS Default Domain Suffix
- DNS Split Network Domain List
- WINS Servers
- PFS Group
- Remote Network Topology
- Login Banner
Gateway Configuration
This example assumes you have knowledge of the Cisco ASA gateway command line configuration interface. For more information, please consult your Cisco product documentation.
Interfaces
Two network interfaces are configured. The outside interface has a static public IP address of 1.1.1.20 which faces the internet. The inside interface has a static private IP address that faces the internal private network. The default gateway is configured as 1.1.1.3 via the outside interface.
Access List
An access lists must be configured to define the IPSec policies. This is expressed with the source matching the local private network(s) and the destination matching any as the VPN client address will be assigned by the gateway.
Address Pool
The IP address pool must be configured. Clients will be assigned private network addresses from a pool of 10.2.20.1-10.2.20.126.
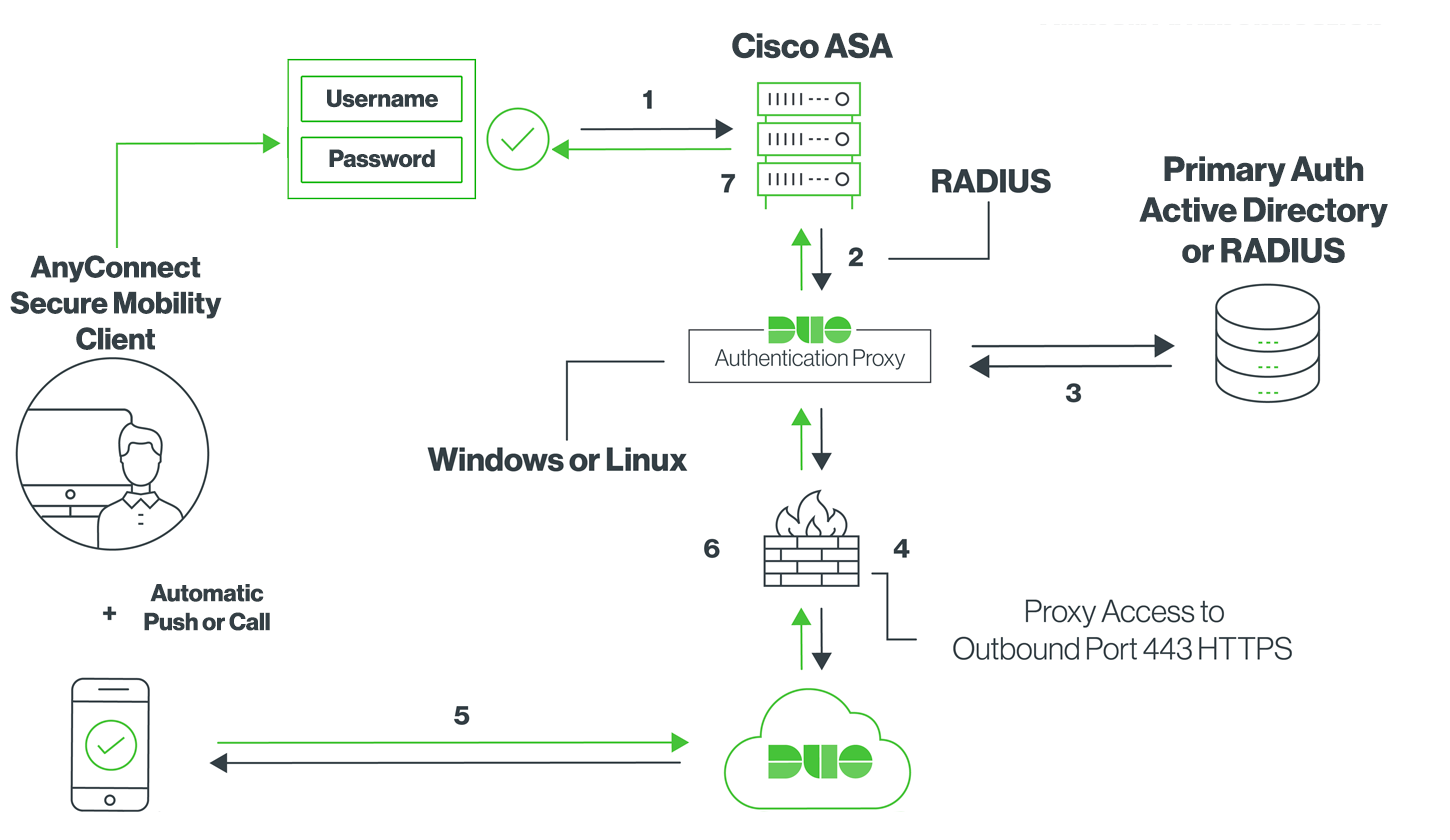
User Authentication
User authentication must be configured to support IKE extended authentication ( XAuth ). In this example, we use define user accounts locally on the ASA. It is possible to pass this authentication to a radius or an LDAP account server using the Cisco AAA authentication mechanism. For more information, please consult your cisco product documentation.
IPsec Parameters
A transform set and dynamic IPsec crypto map must be configured to support client VPN connections. The dynamic crypto map is then assigned to a standard crypto map and bound to the outside ( public ) interface.
ISAKMP Parameters
The ISAKMP protocol must be enabled on the outside ( public ) interface and an ISAKMP policy must be configured. NAT Traversal is also enabled to allow clients to communicate effectively when their peer address is being translated. The keep alive packet rate is set to 20 seconds.
Group Policy
A group policy must be configured to provide the client with dynamic configuration information.
Tunnel Group
A tunnel group must be configured to define the VPN Client tunnel parameters. It is created using the type ipsec-ra for IPsec remote access. The client uses the tunnel group name as its FQDN identity value and the tunnel group pre-shared-key as its pre-shared key value.
Client Configuration
The client configuration in this example is straight forward. Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs.
General Tab
The Remote Host section must be configured. The Host Name or IP Address is defined as 10.1.1.20 to match the ASA outside ( public ) interface address. The Auto Configuration mode should be set to ike config pull.
Cisco Asa Ssl Vpn Configuration
Phase 1 Tab
The Proposal section must be configured. The Exchange Type is set to aggressive and the DH Exchange is set to group 2 to match the ASA ISAKMP policy definition.
Authentication Tab
The client authentication settings must be configured. The Authentication Method is defined as Mutual PSK + XAuth.
Local Identity Tab
The Local Identity parameters are defined as Fully Qualified Domain Name with a FQDN String of 'vpnclient' to match the ASA tunnel group name.
Remote Identity Tab
The Remote Identity parameters are set to IP Address with the Use a discovered remote host address option checked to match the ASA ISAKMP identity parameter.
Credentials Tab

The Credentials Pre Shared Key is defined as 'mypresharedkey' to match the ASA tunnel group pre-shared-key.
Known Issues
Cisco Asa Vpn
Cisco gateways support a proprietary form of hybrid authentication which does not conform to RFC draft standards. At this time the Shrew Soft VPN Client does not support this authentication mode. We hope to add support for this in the future.
Resources
Asa Vpn Clientless
Media:Ciscoasa.cfg.txt
Media:Ciscoasa.vpn.txt
Cisco Asa Vpn Client Download
